未来清晰又迷茫,不知如何去做
前言
挖矿前几年比较火。目前识别挖矿的方法有:协议、流量特征、行为。产品里已经存在相关规则了,那这里就简单说明一下吧。
挖矿协议
挖矿机器与矿池之间的通信需要遵循特定的协议,目前主流的挖矿协议为 Stratum 协议,在很久之前还有 GBT(getblocktemplate)协议和 getwork 协议,不过由于带宽和性能的消耗较多,多年前就已经被新的矿机所抛弃。回到 Stratum 协议,该协议在 2012 年推出,是从 getwork 协议的基础上演变而来的,解决了 getwork 协议效率低下的问题。在 Stratum 中,挖矿机器与矿池之间采用 TCP 的形式传输数据,数据传输的过程基于 JSON-RPC(一个无状态且轻量级的远程过程调用 RPC 传送协议)。矿机向矿池可使用如下 8 个发放发送数据:

矿机
矿池向矿机则可使用如下7个方法发送数据:
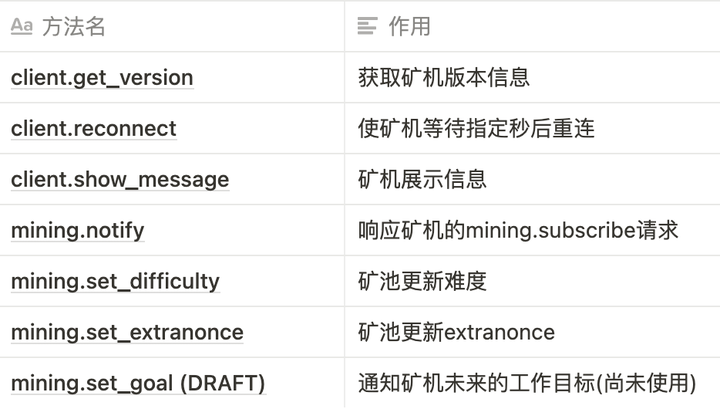
矿池
流量特征
门罗币采用Cryptonight算法,公开提供的程序有xmr-stak,xmrig,claymore等,相应的主要流量请求特征为:
xmr-stak
request:
{"method":"login","params":{"login":"xxxxxxx","pass":"xxx","rigid":"","agent":"xxxxxx"},"id":1}
{"method":"submit","params":{"id":"xx","job_id":"xxxxxx","nonce":"xxxxx","result":"xxxxxx"},"id":1}
response:
{"method":"job","params":{"target":"xxxxx","job_id":"xxxxxx","blob":"xxxxxxx"}}
xmrig
request:
{"id":x,"jsonrpc":"2.0","method":"login","params":{"login":"xxxxxx","pass":"x","agent":"xxxxx","algo":["xxx","xxx","xxx"]}}
{"id":x,"jsonrpc":"2.0","method":"submit","params":{"id":"xxxx","job_id":"xx","nonce":"xxxx","result":"xxxxxxx"}}
response:
{"params":{"blob":"xxxxxx","taget":"xxxx","job_id":"xxxxx"},"method":"xxx"}
claymore
request:
{"method":"login","params":{"login":"xxxxxx","pass":"x","agent":"xxx"},"id":1}
{"method":"submit","params":{"id":"xxxx","job_id":"xxx","nonce":"xxxxx","result":"xxxxx"},"id":x}
response:
{"params":{"blob":"xxxxxx","target":"xxxx","job_id":"xxx"},"method":"xxx"}对上面的流量请求特征分析可以发现,请求中主要分为 login 操作与submit 操作,对具体请求具体分析。login 操作可以分为直接使用 stratum 协议与通过 jsonrpc 方式,suricata 本身有相应检测规则:
alert tcp $HOME_NET any -> $EXTERNAL_NET any (msg:"ET POLICY Crypto Coin Miner Login"; flow:to_server,established; content:"|7b 22|method|22 3a|"; depth:10; fast_pattern; content:"|22|login|22 2c|"; distance:0; within:9; content:"|22|params|22 3a|"; distance:0; within:10; content:"|7b 22|login"; nocase; distance:0; within:8; content:"agent|22 3a|"; nocase; distance:0; metadata: former_category POLICY; reference:md5,d1082e445f932938366a449631b82946; reference:md5,33d7a82fe13c9737a103bcc4a21f9425; reference:md5,ebe1aeb5dd692b222f8cf964e7785a55; classtype:trojan-activity; sid:2022886; rev:3; metadata:affected_product Any, attack_target Client_Endpoint, deployment Perimeter, tag Bitcoin_Miner, signature_severity Audit, created_at 2016_06_09, malware_family CoinMiner, performance_impact Low, updated_at 2017_10_12;)
alert tcp-pkt $HOME_NET any -> $EXTERNAL_NET any (msg:"ET POLICY Cryptocurrency Miner Checkin"; flow:established,to_server; content:"|7b 22|id|22 3a|"; nocase; depth:6; content:"|22|jsonrpc|22 3a|"; nocase; distance:0; content:"|22 2c 22|method|22 3a 22|login|22 2c 22|params|22 3a|"; fast_pattern; content:"|22|pass|22 3a 22|"; nocase; content:"|22|agent|22 3a 22|"; nocase; content:!"<title"; nocase; content:!"<script"; nocase; content:!"<html"; nocase; metadata: former_category POLICY; classtype:policy-violation; sid:2024792; rev:4; metadata:affected_product Windows_XP_Vista_7_8_10_Server_32_64_Bit, attack_target Client_Endpoint, deployment Perimeter, signature_severity Minor, created_at 2017_10_02, updated_at 2018_06_15;)对 submit 操作可以分析,可以使用以下规则进行检测:
alert tcp $HOME_NET any -> $EXTERNAL_NET any (msg:"Cryptocurrency Miner Check By Submit"; flow:to_server,established; content:"|22|method|22 3a|"; fast_pattern; content:"|22|submit|22 2c|"; distance:0; within:10; content:"|22|params|22 3a 7b|"; distance:0; within:15; content:"result|22 3a|"; nocase; distance:0; sid:3013015; rev:1; metadata:Detecting Mining Rules;矿池响应矿工的流量检测规则:
alert http $EXTERNAL_NET any -> $HOME_NET any (msg:"ET CURRENT_EVENTS CoinHive In-Browser Miner Detected"; flow:established,from_server; file_data; content:"coinhive.min.js"; nocase; fast_pattern; content:"start"; nocase; distance:0; content:"script"; content:"var"; distance:0; pcre:"/^\s*(?P<var>[a-zA-Z0-9]{3,20})\s*=\s*new\s*CoinHive\s*\.\s*[^\(]+\(\s*[\x22\x27][A-Za-z0-9]+\s*[\x22\x27]\s*(?:\x2c\s*\x7b\s*\w+\x3a\s*\d\.\d\x7d)?\)\s*\x3b\s+(?P=var)\s*\.\s*start/Ri"; metadata: former_category CURRENT_EVENTS; classtype:policy-violation; sid:2024721; rev:2; metadata:affected_product Any, attack_target Client_Endpoint, deployment Perimeter, signature_severity Minor, created_at 2017_09_18, performance_impact Moderate, updated_at 2018_05_08;)挖矿协议如果进行加密,则需要结合威胁情报来辅助监控。